A DIDS Based on The Combination of Cuttlefish Algorithm and Decision Tree
Abstract
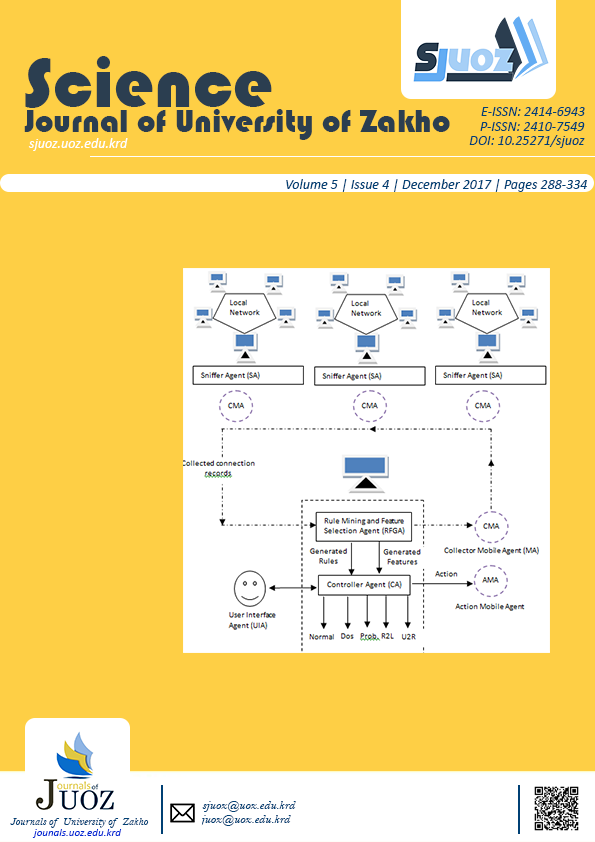
Different Distributed Intrusion Detection Systems (DIDS) based on mobile agents have been proposed in recent years to protect computer systems from intruders. Since intrusion detection systems deal with a large amount of data, keeping the best quality of features is an important task in these systems. In this paper, a novel DIDS based on the combination of Cuttlefish Optimization Algorithm (CFA) and Decision Tree (DT) is proposed. The proposed system uses an agent called Rule and Feature Generator Agent (RFGA) to generate a subset of features with corresponding rules. RFGA agent uses CFA to search for optimal subset of features, while DT is used as a measurement on the selected features. The proposed model is tested on the KDD Cup 99 dataset. The obtained results show that the proposed system gives a better performance even with a small subset of 5 features when compared with using all 41 features.
Full text article
References
Authors
Copyright (c) 2017 Adel S. Eesa, Adnan M. Abdulazeez, Zeynep Orman

This work is licensed under a Creative Commons Attribution 4.0 International License.
Authors who publish with this journal agree to the following terms:
- Authors retain copyright and grant the journal right of first publication with the work simultaneously licensed under a Creative Commons Attribution License [CC BY-NC-SA 4.0] that allows others to share the work with an acknowledgment of the work's authorship and initial publication in this journal.
- Authors are able to enter into separate, additional contractual arrangements for the non-exclusive distribution of the journal's published version of the work, with an acknowledgment of its initial publication in this journal.
- Authors are permitted and encouraged to post their work online.