APPLICATION OF ARTIFICIAL INTELLIGENCE FOR MONITORING DARK WEB ACTIVITIES
Abstract
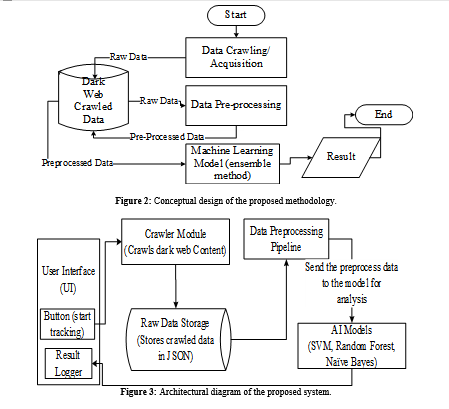
The Dark Web is a hidden part of the internet that attracts perpetrators due to its anonymity. It is used for cybercrime, illegal trading, and by terrorist groups to exchange stolen data and personal information. Current techniques for combating and identifying these concerns are weak. The primary focus of this study is on the application of artificial intelligence to monitor the Dark Web. The solution mitigates monitoring deficiencies to facilitate the timely identification of prospective threats, including data breaches and cybercrimes. The six forms of activities prioritised include cyberterrorism, terrorist activities, weapons trading, drug trafficking, human trafficking, and regular activities. The tasks carried out in this study include crawling relevant data, training machine learning models using an ensemble voting approach, and implementing a JavaScript-powered crawling engine. The AI model is tested and evaluated using data collected from various Onion sites that include both legal and illegal content. The approach used in this study gives 97% accuracy and a macro average precision of 98%. The macro average for recall and f1-score is 97%. The precision, recall and F1-Score all have the same weighted average of 97%.
Full text article
References
Alaidi, A. H. M., Al_airaji, R. M., Alrikabi, H. T. S., Aljazaery, I. A., & Abbood, S. H. (2022). Dark Web Illegal Activities Crawling and Classifying Using Data Mining Techniques. International Journal of Interactive Mobile Technologies (IJIM), 16(10), 122–139. https://doi.org/10.3991/ijim.v16i10.30209
Ali, A., & Qasim, M. (2023). Terrorist Acts on the Surface and Dark Web. In Dark World (pp. 84–101). CRC Press. https://doi.org/10.1201/9781003404330-7
Alshammery, M. K., & Aljuboori, A. F. (2022). Crawling and Mining the Dark Web: A Survey on Existing and New Approaches. Iraqi Journal of Science, 1339–1348. https://doi.org/10.24996/ijs.2022.63.3.36
Basheer, R., & Alkhatib, B. (2021). Threats from the Dark: A Review over Dark Web Investigation Research for Cyber Threat Intelligence. Journal of Computer Networks and Communications, 2021, 1–21. https://doi.org/10.1155/2021/1302999
Ebrahimi, M., Nunamaker, J. F., & Chen, H. (2020). Semi-Supervised Cyber Threat Identification in Dark Net Markets: A Transductive and Deep Learning Approach. Journal of Management Information Systems, 37(3), 694–722. https://doi.org/10.1080/07421222.2020.1790186
Fang, Y., Guo, Y., Huang, C., & Liu, L. (2019). Analyzing and Identifying Data Breaches in Underground Forums. IEEE Access, 7, 48770–48777. https://doi.org/10.1109/access.2019.2910229
Ghosh, S., Das, A., Porras, P., Yegneswaran, V., & Gehani, A. (2017). Automated Categorization of Onion Sites for Analyzing the Darkweb Ecosystem. Proceedings of the 23rd ACM SIGKDD International Conference on Knowledge Discovery and Data Mining, 1793–1802. https://doi.org/10.1145/3097983.3098193
He, S., He, Y., & Li, M. (2019). Classification of Illegal Activities on the Dark Web. In Proceedings of the 2019 2nd International Conference on Information Science and Systems (Vol. 54, pp. 73–78). ACM. https://doi.org/10.1145/3322645.3322691
Huang, C., Guo, Y., Guo, W., & Li, Y. (2021). HackerRank: Identifying key hackers in underground forums. International Journal of Distributed Sensor Networks, 17(5), 155014772110151. https://doi.org/10.1177/15501477211015145
Kaur, S., & Randhawa, S. (2020). Dark Web: A Web of Crimes. Wireless Personal Communications, 112(4), 2131–2158. https://doi.org/10.1007/s11277-020-07143-2
Mahmood, I., Rahman, M. A., Kabir, M. A., & Shahriar, M. (2022). A Survey on Dark Web Monitoring and Corresponding Threat Detection. October. https://www.researchgate.net/publication/364898748
Saini, J. K., & Bansal, D. (2019). A Comparative Study and Automated Detection of Illegal Weapon Procurement over Dark Web. Cybernetics and Systems, 50(5), 405–416. https://doi.org/10.1080/01969722.2018.1553591
Schafer, M., Fuchs, M., Strohmeier, M., Engel, M., Liechti, M., & Lenders, V. (2019). BlackWidow: Monitoring the Dark Web for Cyber Security Information. In 2019 11th International Conference on Cyber Conflict (CyCon). IEEE. https://doi.org/10.23919/cycon.2019.8756845
Wiafe, I., Koranteng, F. N., Obeng, E. N., Assyne, N., Wiafe, A., & Gulliver, S. R. (2020). Artificial Intelligence for Cybersecurity: A Systematic Mapping of Literature. IEEE Access, 8, 146598–146612. https://doi.org/10.1109/access.2020.3013145
yang, Y., Zhu, G., Yang, L., & yu, H. (2020). Crawling and Analysis of Dark Network Data. In Proceedings of 2020 6th International Conference on Computing and Data Engineering (Vol. 24, pp. 116–120). ACM. https://doi.org/10.1145/3379247.3379272
Zenebe, A., Shumba, M., Carillo, A., & Cuenca, S. (2019). Cyber Threat Discovery from Dark Web. EPiC Series in Computing, 174–163. https://doi.org/10.29007/nkfk
Authors
Copyright (c) 2026 Abimbola G. Akintola1 , Yusuf O. Olatunde2, ∗ , Kolawole Y. Obiwusi3 , Ganiyat K. Afolabi-Yusuf3 , Muhammed A. Adebisi3 , Ayobami A. Tewogbade2 , Lawrence O. Omotosho4 , Olajide Y. Adebayo4 and Aminat A. Oladipo-Tanimowo4

This work is licensed under a Creative Commons Attribution-NonCommercial-ShareAlike 4.0 International License.
Authors who publish with this journal agree to the following terms:
- Authors retain copyright and grant the journal right of first publication with the work simultaneously licensed under a Creative Commons Attribution License [CC BY-NC-SA 4.0] that allows others to share the work with an acknowledgment of the work's authorship and initial publication in this journal.
- Authors are able to enter into separate, additional contractual arrangements for the non-exclusive distribution of the journal's published version of the work, with an acknowledgment of its initial publication in this journal.
- Authors are permitted and encouraged to post their work online.